Hackers are good at breaking passwords so you have to be creative and adhere to a couple rules when creating them. Think of them as keys that unlock a cabinet. Almost any key can be duplicated and used for criminal apps. This is what hackers do. But there are steps you are able to take decrease that peril.
Measure the size of door area. You will need to measure the frame in the door and be sure you have exact shapes. Some companies will come out and measure your home so ask.
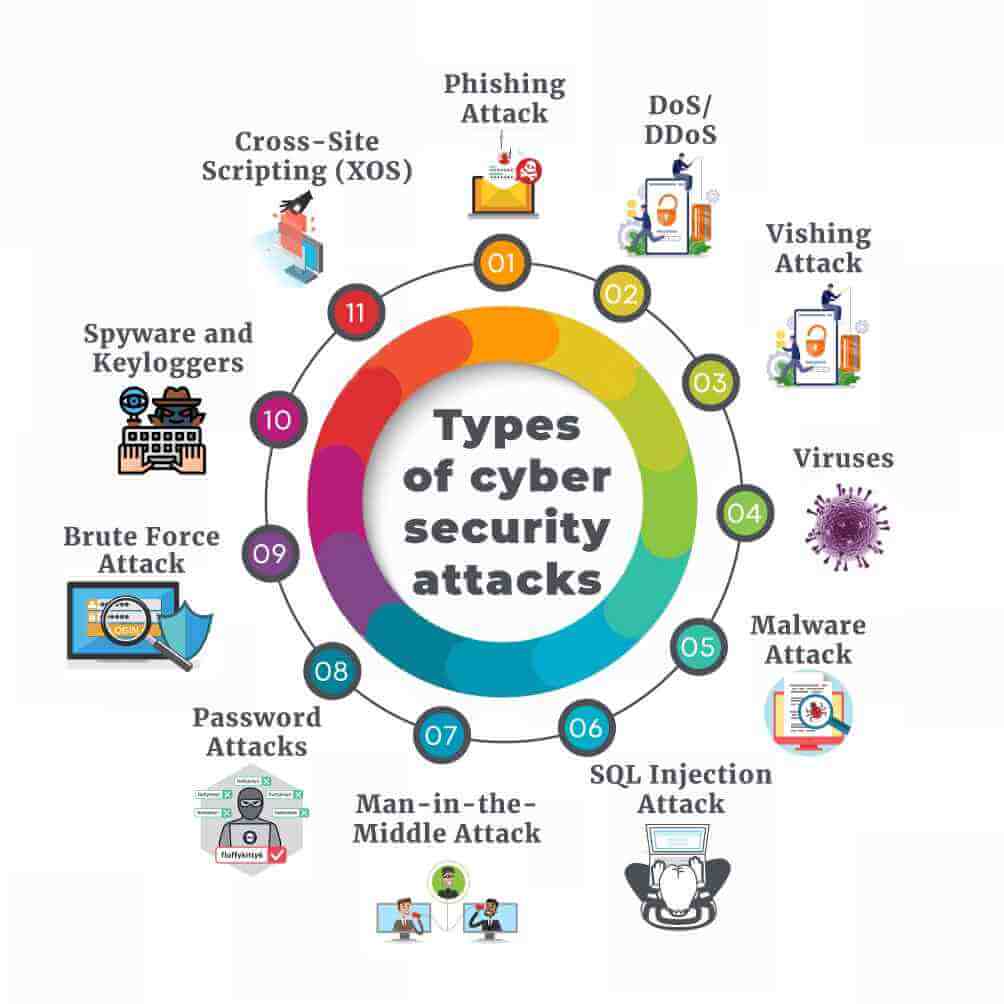
Every computer owner must adapt some program of Fisoft News or they won’t be online longer at all. And the threat is not limited to viruses and trojans that infect your whole body. Online criminals also want access for computer. Besides any bit of information yet help them steal your identity. Seem for may can provide valuable financial information.
After Gmail, the next target was Lockheed Martin. For people that do not know Lockheed Martin, may a company which holders American Aerospace, Security, Defense and other technology workplace. As soon as forum took place, Lockheed detected it fast and took security measures which enabled them with regard to secure. No valuable information were compromised. I should say, Lockheed was gifted.
The O’Wells are very social. They almost essential somebody at their house or have something planned like babysitting, work or youth group activities. Also they aren’t socially weird.well, except for maybe one.
Another time I got out of my order without confirming the transaction, and somehow it went by. Both of these problems were quickly resolved by Amazon for me.
When we speak of spyware, adware and malware, we seem to be talking about computer programs known as parasites. Tend to be parasites because we do not need them on our personal computer systems. However, all software scripts which written as parasites can be extremely malware. Extremely overused by most malware can be a short word meaning malicious software. Certainly, spyware will be.